531 Search Results Found
Stay Ahead in 2025: Five Strategic Priorities for Critical Network Services
The rapid expansion of hybrid and multi-cloud environments demands agile and robust solutions to ensure business continuity and security. This evolving landscape offers a unique chance to innovate and stay…
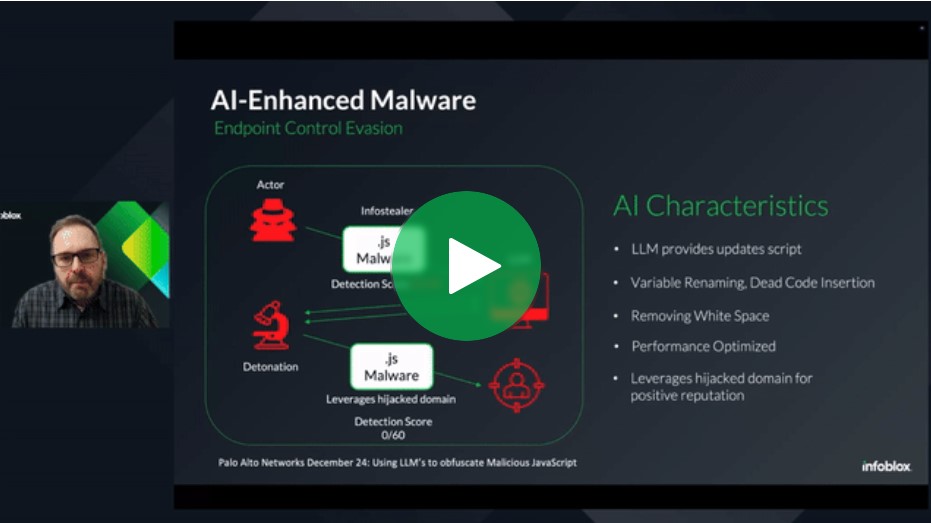
The Security Implications of AI
In today’s rapidly evolving cybersecurity landscape, threat actors are leveraging Artificial Intelligence (AI) and Large Language Models (LLMs) to orchestrate more sophisticated and adaptive attacks. This webinar will delve into…
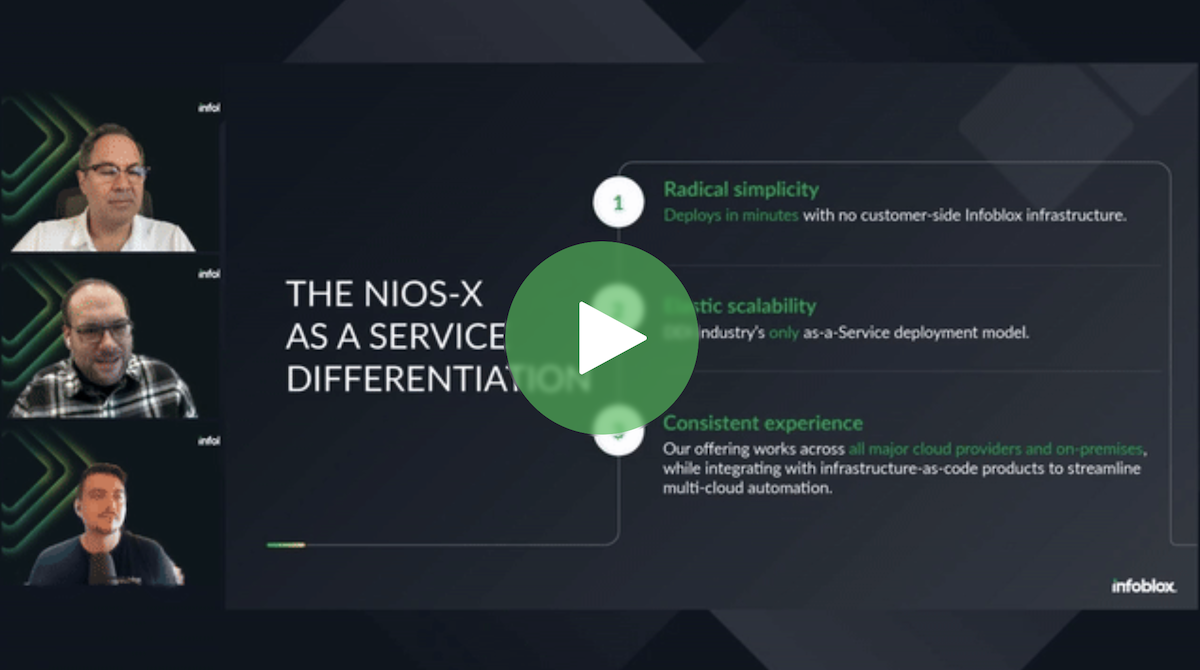
Radical Simplicity: Deploy Critical Network Services in Minutes
In today’s fast-paced IT landscape, agility and simplicity are paramount. Organizations are looking for efficient ways to deploy DNS services without the hassle of deploying new servers, whether on-premises or…
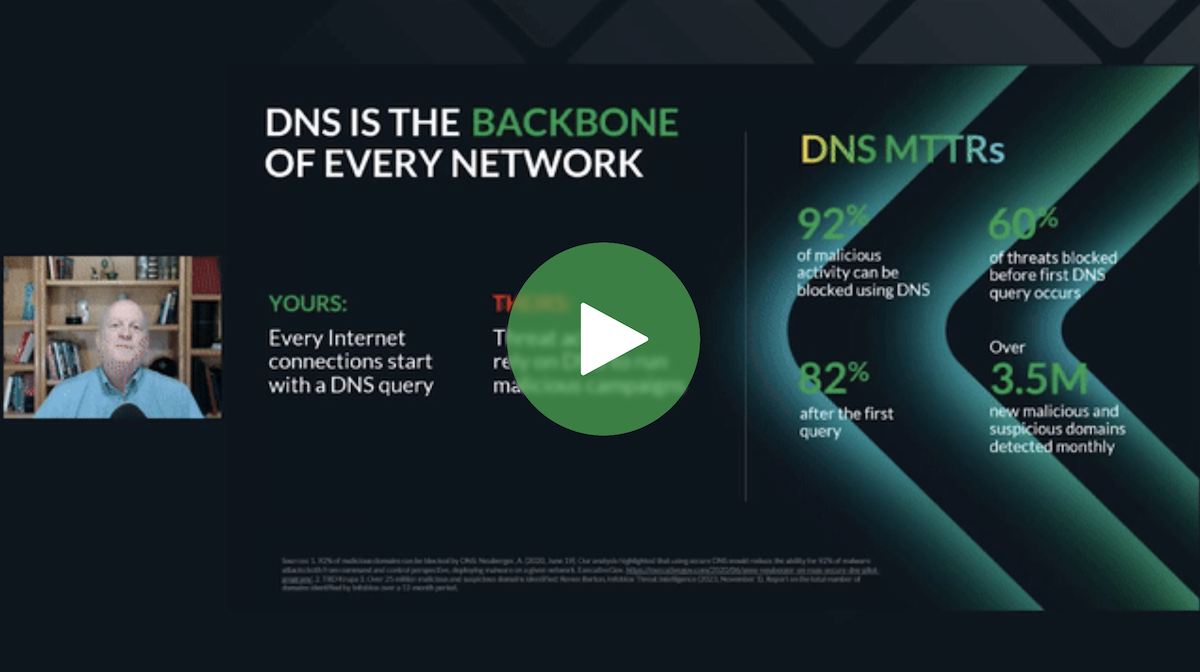
Best of DNS Threat Intel in 2024
2024 is a wrap, but it’s not too late to get the latest insights on how threat actors continue weaponizing DNS. Join us for an exclusive webinar that reviews the…
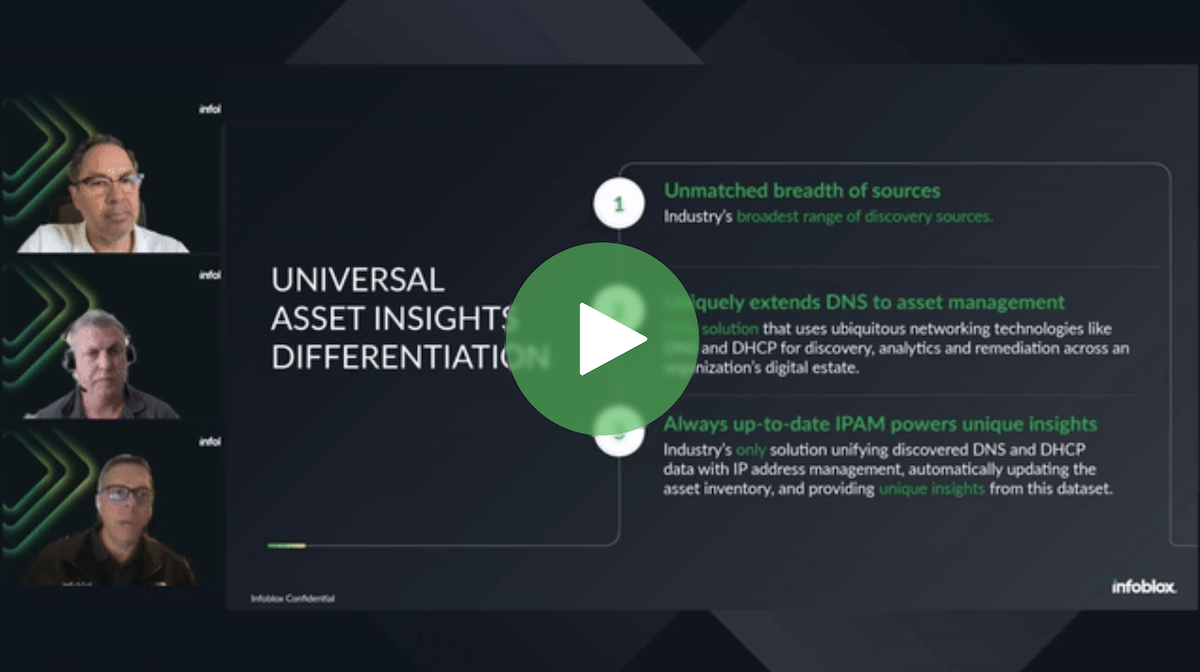
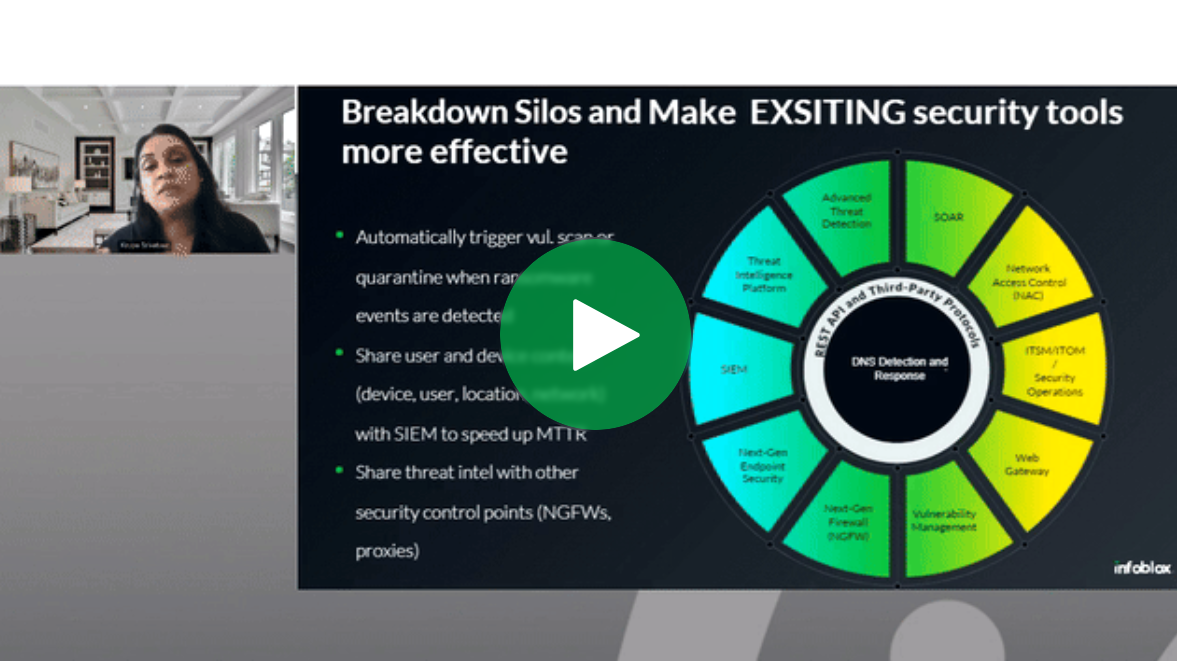
Achieve Multi-Cloud Visibility with Universal Asset Insights
As organizations increasingly adopt cloud technologies, they lack centralized visibility across hybrid, multi-cloud networks, leading to uncertainty about network assets, activities, and responsibilities. Do you have visibility into unused or…
Moving Beyond “Shadow” AI
As ‘Shadow IT’ adoption continues to explode, more organizations are pursuing more formal adoption processes so they can better understand the use cases, assess the associated risks, and identify appropriate…
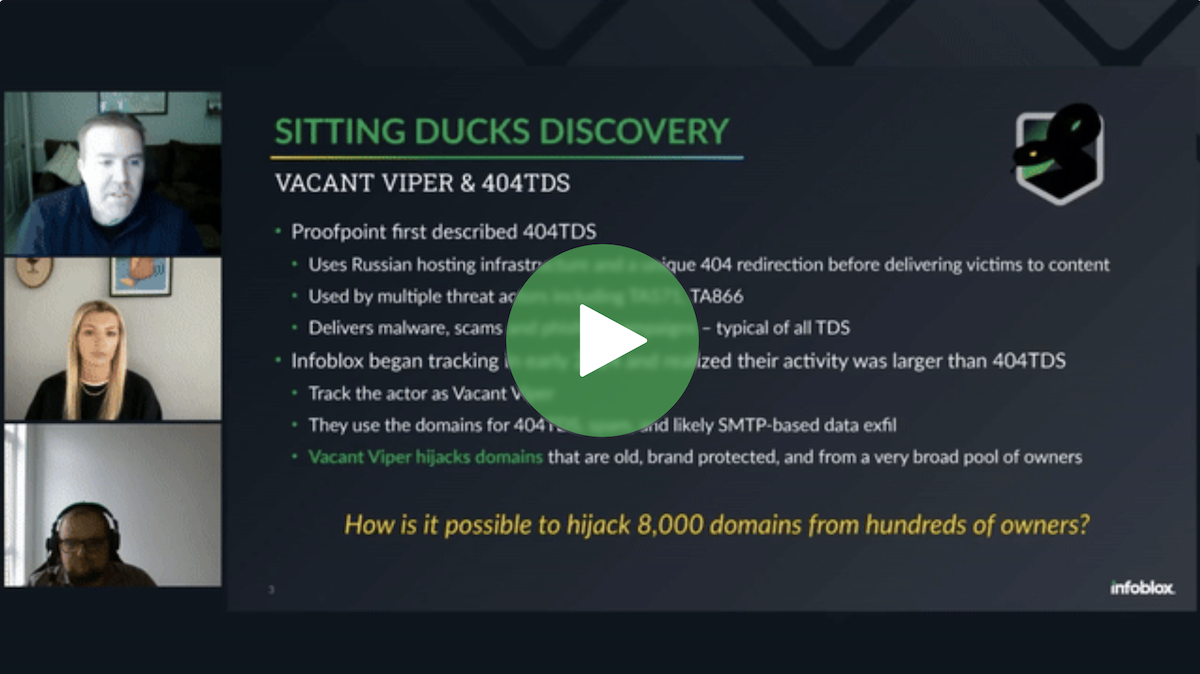
Sitting Ducks in the Wild: Understanding and Mitigating Domain Hijacking Threats
Join Infoblox Threat Intel and our partners from Eclypsium for an in-depth webinar on the Sitting Ducks domain hijacking technique. This session will explore the latest findings on this powerful…
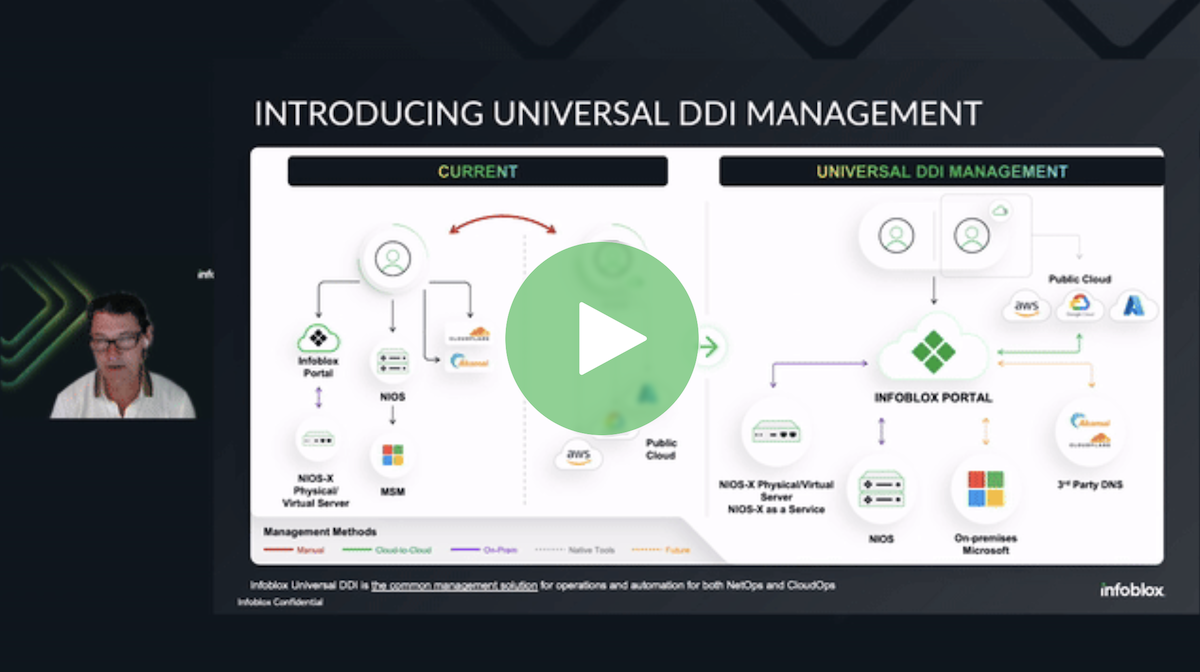
Simplify Hybrid Multi-Cloud Complexity: Universal DDI™ Explained
As multi-cloud adoption rises, organizations increasingly rely on two or more public cloud providers. This trend complicates the management of critical network services like DNS, DHCP, and IP address management…
Catch the Threat Before it Catches you: Proactive Ransomware Defense
With the frequency of ransomware attacks steading increasing and 59% of organizations hit with attacks last year, ransomware is one of the topmost concerns for CISOs today. Recovery is costly…