494 Search Results Found
Evolving DNS as Part of Your XDR Strategy
Today’s networks have evolved from static, centralized environments to a highly distributed infrastructure spanning multi-cloud, on-premises, edge, and IoT/OT environments. With this increasing complexity, the ability to provide comprehensive protection…
ThreatTalk Season 3 Episode 3 | Emails That Say “ILOVEYOU”: Lessons Learned from the Love Bug Virus
Emails that say lessons learned from the love bug Virus
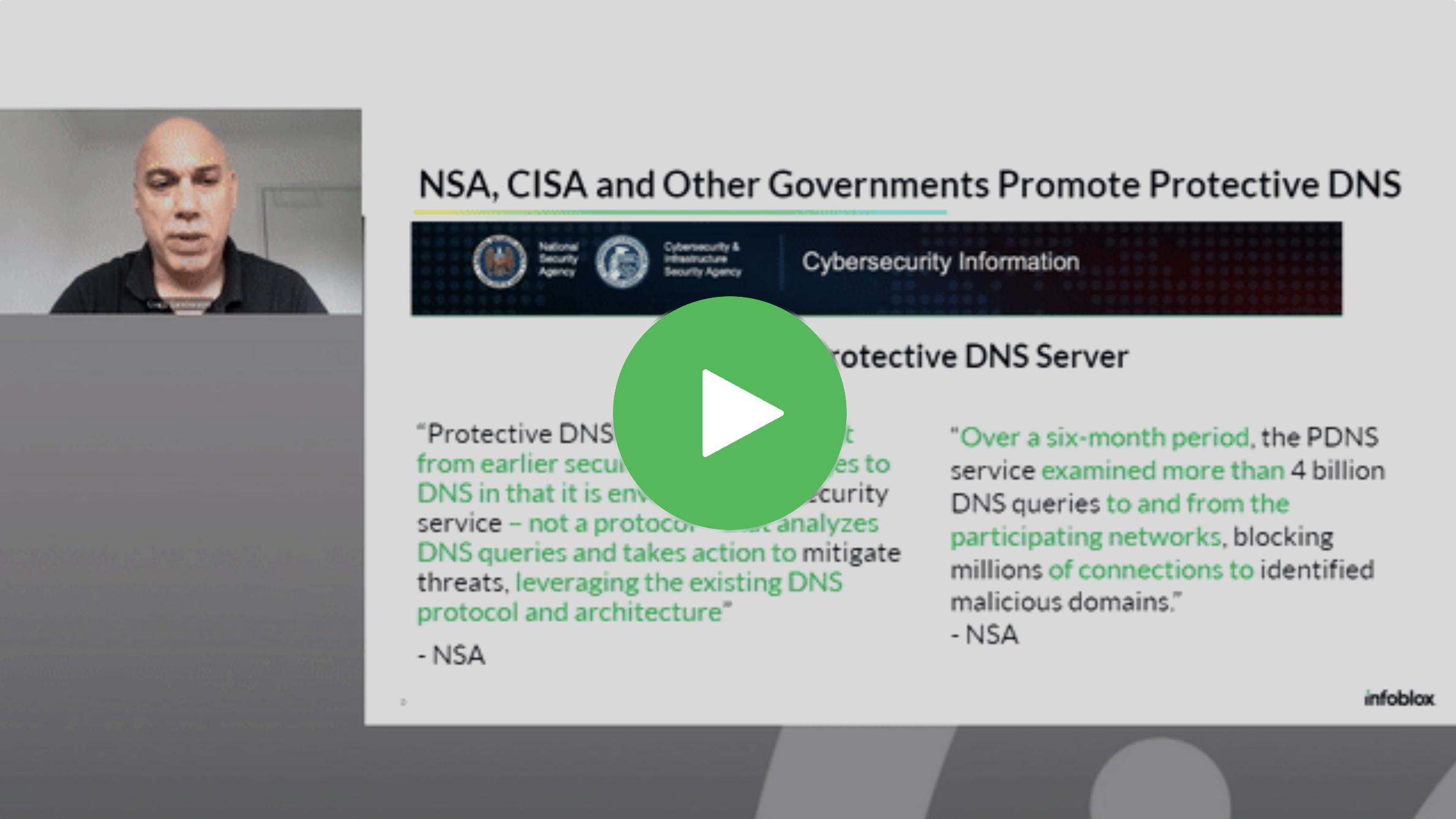
Enhancing DNS Security: Implementing Encrypted DNS to Meet CISA Guidelines
In response to the CISA Guidance, federal agencies are now required to encrypt DNS traffic and use Protective DNS for egress DNS resolution. Join our informative webinar where we will…
ThreatTalk Season 3 Episode 19 | RE:Bots in Disguise-Detecting Cyberthreat Camouflage
Re:Bots in Disguise-Detecting
The Hidden Potential of DNS in Security
The book The Hidden Potential of DNS in Security reveals how attackers exploit DNS and how cybersecurity professionals can proactively use DNS to turn the tables and mitigate those threats.…
SMS Cybercrime: A DNS Perspective
As email protection has increased, criminals have moved to attack users through SMS and other text messaging services. The cost to consumers of SMS scams alone was $330 million in…
ThreatTalk Season 3 Episode 4 | Let’s Dwell a Moment on “Dwell Time”
Let’s Dwell a Moment on
ThreatTalk Season 3 Episode 20 | Bringing Shadow IT into the Light
IT into the Light
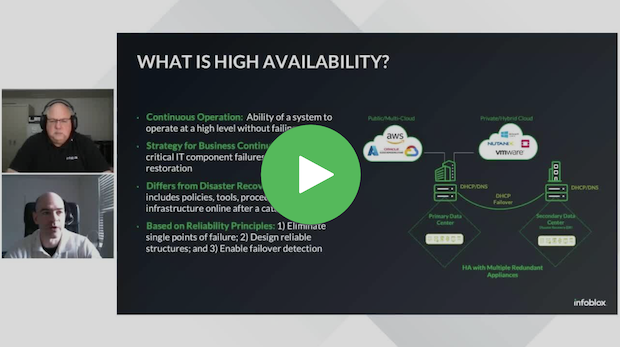
Driving Resiliency and Automation in Hybrid Multi-Cloud Environments
How do you ensure network resiliency and automation in hybrid, multi-cloud environments? Join this webinar to learn how to leverage DNS, DHCP, and IPAM (DDI) using alternative High Availability (HA)…