DDoS Attacks
There are many types of distributed denial of service (DDoS) attacks. We see them in the news these days, often accompanied by a ransom to induce the attacker to stop the DDoS attack. When it comes to DNS, we can look at specific types of attacks that are used to overwhelm DNS servers, thus rendering the DNS service unavailable. When an attack on the DNS is successful, it can bring an organization to a screeching halt. When a company can’t publish the addresses for its web and mail servers, business stops.
The two main DDoS attack methodologies we want to look at are amplification and reflection. While technically two different attack tactics, attackers often combine amplification and reflection attacks.
Amplification DDoS Attacks
An amplification attack is a technique where a small query can trigger a large response, such as querying for a TXT record or a zone transfer when you haven’t secured zone transfers to only your trusted sources. By flooding the server with short requests that require long responses, even a relatively weak computer can overload a DNS server. The DNS server is so busy doing the heavy lifting to respond to all these bogus requests that it doesn’t have time to respond to legitimate ones.
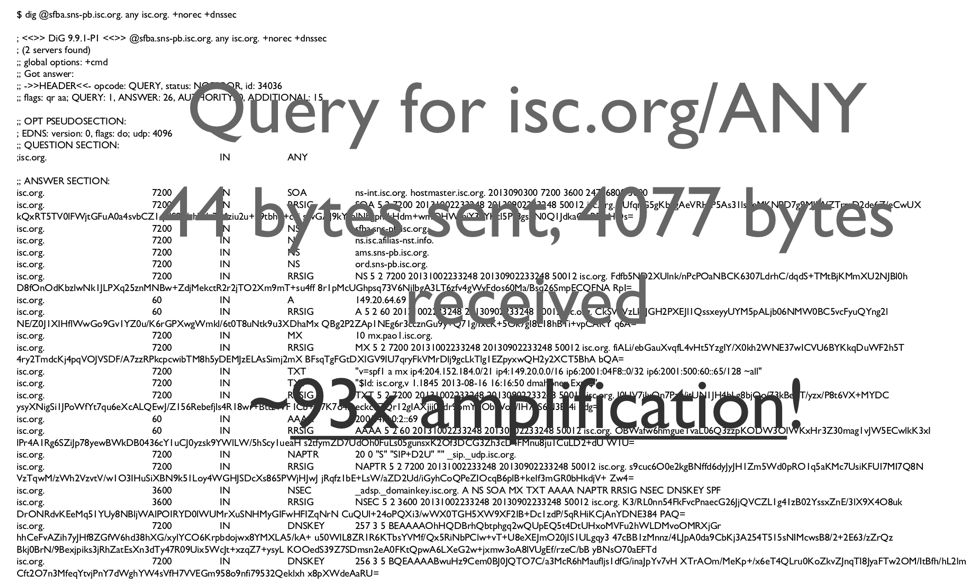
DNS servers make surprisingly good amplifiers. Figure 2-1 shows a simple example:
If a user makes a DNS query for “isc.org/ANY”, the query is 44 bytes long, and the response is 4077 bytes long. That is around 93 times amplification!
Figure 2-1: Amplification example of querying isc.org/any
This example and some simple math show how devastating amplification can be. Say an attacker is generating queries with a botnet (a network of independent hosts, or bots, infected with malware) , and each bot has a measly 1 Mbps connection to the Internet: With a 1 Mbps connection, each bot could send the 44 byte query from the previous example approximately 2909 times per second.
Because each query results in a response that is 4077 bytes, you can calculate that the DNS server has to come up with about 93 Mb each second.
If the botnet contains 11 bots all doing the same thing, that’s a total of over 1 Gb that the DNS server is supposed to send out every second of the attack!
Amplification alone makes an effective attack, because attackers can use less powerful resources to overload more powerful servers. However, what makes DNS an even more devious target for DDoS is reflection.
Reflection DDoS Attacks
A reflection attack sends queries that look like they came from the victim of the attack. The response (often a large, amplified answer) is sent to the victim, who never asked, and the amount of the response traffic could potentially overwhelm the victim’s network.
In a reflection attack, an attacker sends a query to a recursive name server with a spoofed source IP address. Instead of his real IP address, he places the target (victim) IP address as the source IP address. The recursive name server does the legwork, retrieves the answer to the query from the authoritative name server, and sends the answer to the unsuspecting victim.
Combination DDoS Attacks
Now the attacker combines the two techniques by spoofing the victim’s IP address and sending a carefully crafted query that will result in a large payload. This is a very effective DDoS attack; the authoritative name server provides the amplification, and the recursive name server provides the reflection. This allows the attacker to attack two different victims at the same time. It also causes the victim of the amplification attack to possibly believe they were attacked by the second victim, causing potentially even more mayhem.
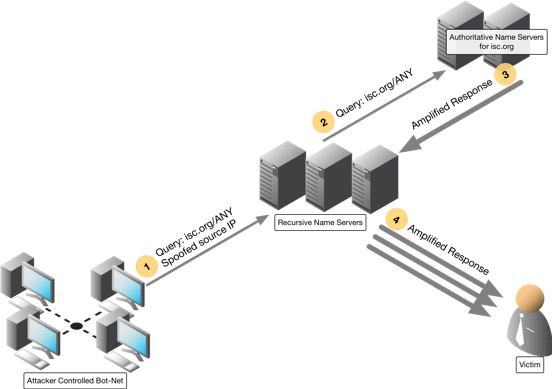
Figure 2-2: An amplified reflection attack. As you can see, this attack consumes the resources of not only the victim, but also those of the recursive name servers. This is why securing a publicly facing recursive server against recursion from the world, is one of the most important best practices in DNS Security. It prevents you from playing the role of amplifier.
Walking through the steps in Figure 2-2 we see the following play out
- An attacker-controlled botnet sends DNS queries with a victim’s spoofed IP address to recursive name servers.
- Recursive name servers follow the standard DNS path and send the query to other authoritative name servers.
- Recursive name servers receive the (amplified) response from authoritative servers.
- Recursive name servers send the (amplified) response to the victim, whose IP address was listed as the source address in the original query.
Mitigation solutions exist for both reflection and amplification methods of DDoS attach. To learn more, we invite you to download our free DNS Security for Dummies ebook.